Was this page helpful?
Deploy ScyllaDB to Your Own Cloud Account - GCP¶
Available with the Professional plan and above
When you select Google Cloud Platform as your cloud provider when creating a cluster, your cluster is deployed by default under the ScyllaDB GCP account. As an alternative, you can deploy the ScyllaDB Cloud database into your own GCP account—a model referred to as Bring Your Own Account (BYOA).
This article will guide you through the process of integrating your GCP account with ScyllaDB Cloud.
Caution
ScyllaDB Cloud creates resources within your account and assumes exclusive management of those resources.
If you modify any infrastructure components managed by ScyllaDB Cloud, we cannot guarantee that the service will continue to operate as expected. This includes modifications to security groups, permissions associated with the ScyllaDB role, or other restrictions that could disrupt ScyllaDB Cloud’s ability to manage the necessary resources. Such changes may affect our ability to uphold service commitments within your account.
To avoid service disruptions, please consult our support team before making any changes to ScyllaDB-managed resources.
Prerequisites¶
Verify that the recommended limits are set for your GCP account.
Linking Your GCP Account with ScyllaDB Cloud¶
Before you provision a cluster in your GCP account, you must link that account with ScyllaDB Cloud.
To make linking easier, we will provide you with a terraform template. You will need terraform and GCP permissions to grant all required permissions.
A wizard will guide you through the process.
Go to Managed Resources via the drop-down in the top right corner next to your username.
Open the Bring Your Own Account tab.
Click Add Account to open the Add Cloud Account wizard.
Choose your Google Cloud Platform from the Provider drop-down.
In the Project ID field, specify your project ID.
You can copy your project ID from the Google Cloud Console.
Click Generate Template to generate a Terraform template that includes all files required for provisioning the cloud resources.
Click Next to open a screen displaying further instructions and the Cloud Resource Template Secret that will be required while applying the Terraform template.
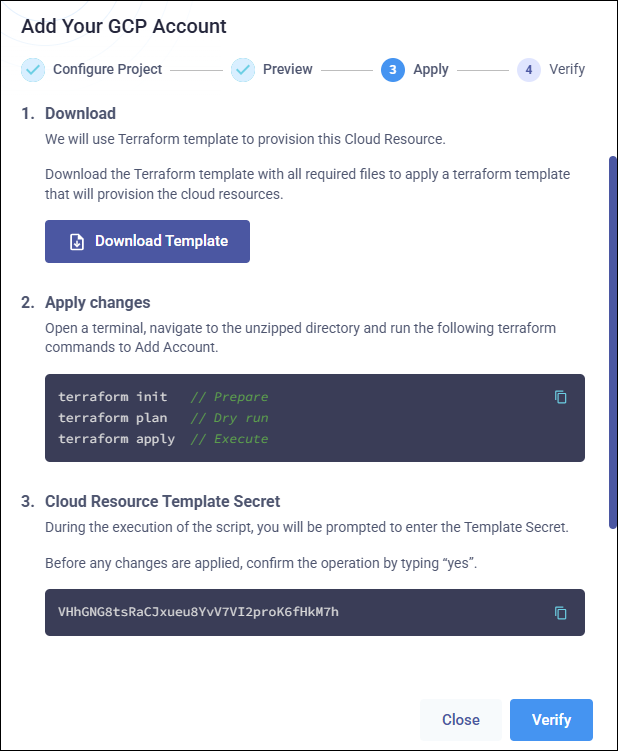
Click Download template to download the Terraform template (a ZIP archive).
Unzip the archive.
In a terminal, navigate to the unzipped directory and run the following terraform commands to set up the account.
To initialize Terraform:
terraform init
To dry run:
terraform plan
To apply the changes:
terraform apply
When running
terraform initandterraform plan, you will be prompted to enter the Cloud Resource Template Secret: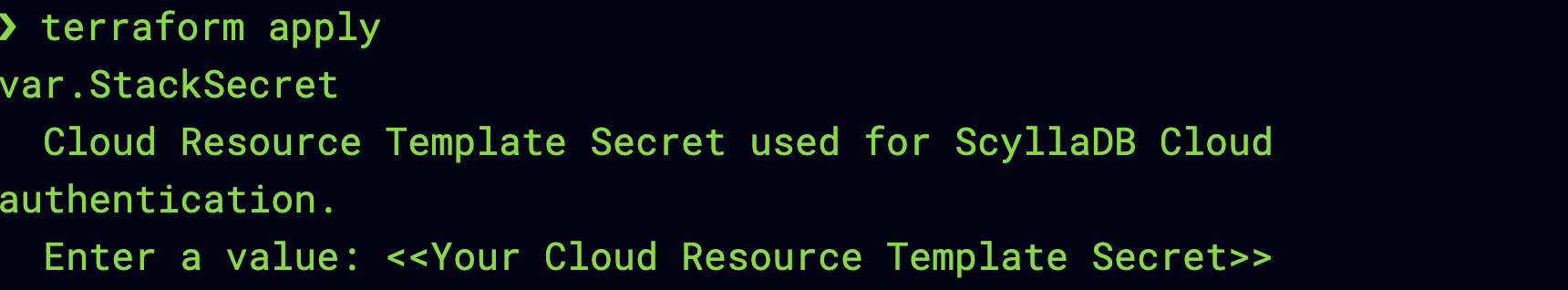
Copy and paste the Cloud Resource Template Secret from the wizard:
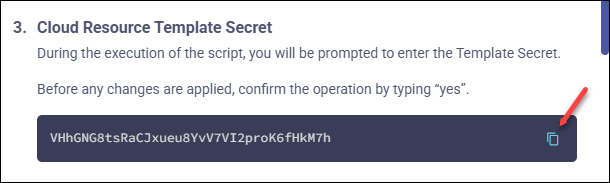
Go back to the wizard and click Verify to verify that your GCP account has been set up correctly.
(Optional) While waiting for verification to complete, you can add a custom alias for your account. A user-friendly identifier is helpful if your ScyllaDB account is connected to multiple AWS accounts to clearly identify and manage each account.
Once Terraform completes successfully and verification is confirmed, your GCP account is ready to be used for the deployment of ScyllaDB clusters. When you select the Your GCP Account option during cluster creation, the new account will be available in the drop-down (either the alias, if provided, or the Project name will be displayed).
To add another GCP account, repeat the steps above. You can link multiple GCP accounts to one ScyllaDB Cloud account.
Reviewing and Managing Your Accounts¶
To review the list of your accounts linked with ScyllaDB Cloud, go to Managed Resources via the drop-down and open the Bring Your Own Account tab.
It will display the following information:
Alias - A user-friendly name for your account that simplifies referencing and management. To add or update an alias, click the Actions menu for the account and choose Edit Alias.
Account/Project - The name of your AWS account or GCP Project.
ID - The ID of your account in ScyllaDB Cloud (
byoa_id). It is required to create a cluster using ScyllaDB Cloud API or Terraform.Provider - Your cloud provider name.
Date Added - The date when the account was added to ScyllaDB Cloud.
Status - The status of the account in ScyllaDB Cloud:
Available - The account is added to ScyllaDB Cloud and verified. You can use it when creating a new cluster.
Pending Action - The account has not been provisioned. You can click Resume to finalize your account.
In Use - The account is in use by an existing cluster. You can click the Cluster Name link next to the status to view the information about the cluster.
Deleted - The account has been deleted and cannot be re-used.
Clusters - The list of clusters deployed under this account.
Actions - An actions menu for managing the account. It includes options to delete the account or create an alias for it.
Deleting an Account¶
You can delete an account that is not in use. To delete your account:
Go to Managed Resources via the drop-down and open the Bring Your Own Account tab.
Click the Actions menu for the account you want to delete.
Choose Delete.
This will remove any information associated with that account from ScyllaDB Cloud. Consequently, you won’t be able to use that account to provision new clusters.
Next, you can remove ScyllaDB Cloud resources from your AWS account or GCP project by clicking the Clean Up button displayed for the account you deleted.
GCP Account Limits¶
To ensure that you don’t exceed your GCP account quota, we suggest setting a specific quota for the resources that ScyllaDB Cloud will use. Please note that the recommended limits should be considered in addition to your current resource allocation.
Service Name |
Quota Name |
Recommended Value |
|---|---|---|
Compute Engine API |
VPC networks per project |
5 |
Compute Engine API |
Networks |
20 |
Compute Engine API |
Firewall Rules |
200 |
Compute Engine API |
VM instances |
20 |
Compute Engine API |
CPUs |
10000 (the default is 30000) |
Compute Engine API |
Local SSD (GB) |
10000 (the default is 30000) |
Compute Engine API |
Static external IP addresses per project |
20 |
GCP BYOA Role Permissions¶
This section lists the permissions that ScyllaDB Cloud role requires to deploy and manage your clusters in your GCP account.
Category |
Permision |
|---|---|
Addresses |
|
Disks |
|
Firewall Policies & Rules |
|
Instances (VMs) |
|
Machine Types |
|
Networks & Routing |
|
Subnetworks |
|
Operations |
|
Regions & Zones |
|
Projects (Compute-scoped) |
|
Resources |
|
Category |
Permision |
|---|---|
Roles |
|
Service Accounts |
|
Service Account Keys |
|
Category |
Permision |
|---|---|
Buckets |
|
Objects |
|
